TLDR¶
• Core Points: A user-friendly, open-source macOS authenticator called Mactokio eliminates the need to grab a phone for 2FA codes, integrating token generation directly on the Mac.
• Main Content: The article documents the motivation, design, and implications of replacing mobile-based two-factor authentication codes with a native Mac solution.
• Key Insights: Native desktop authentication can streamline security workflows, but it must balance usability, security, and platform integration.
• Considerations: Security model, key management, phishing resistance, and cross-device recovery are central concerns for any desktop authenticator.
• Recommended Actions: Explore open-source macOS authenticator options, assess your threat model, and ensure strong device security and backup strategies.
Content Overview¶
Two-factor authentication (2FA) codes are a staple of modern online security. For many users, the routine is painful: when prompted for a verification code, they must grab their phone, wake it, unlock it, locate the authenticator app, and read the tiny digits before the timer runs out. If the code is late or missed, the login process stalls, forcing another attempt. This friction can erode security efforts simply because users are discouraged from completing the extra step promptly.
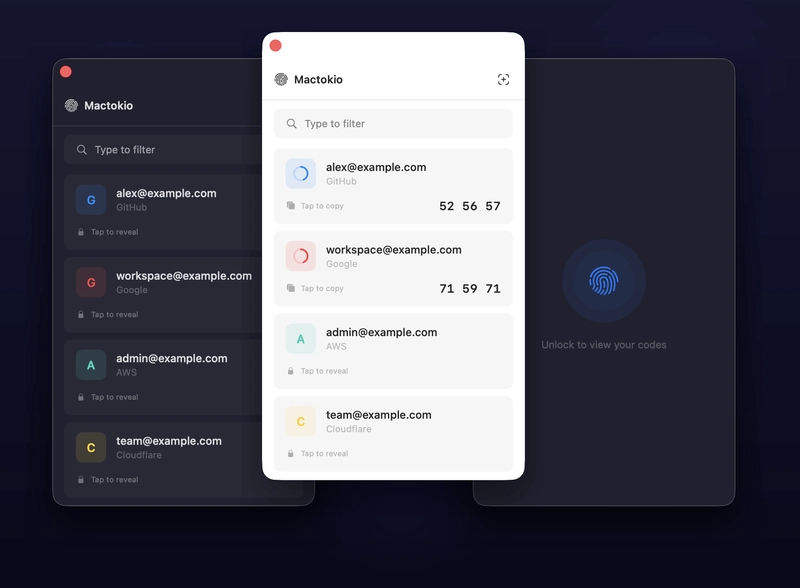
The author of this piece grew tired of the recurring disruption and decided to rethink the user experience. The result is Mactokio, a native macOS authenticator that sits directly on a user’s Mac. Short for Mac + Token + I/O, Mactokio aims to streamline multi-factor authentication by removing the dependency on a mobile device for time-based one-time passwords (TOTPs). It is presented as a free, open-source solution designed to integrate seamlessly into the macOS workflow.
This article outlines what Mactokio is, why it was created, how it functions, and the broader implications of moving 2FA code generation onto the desktop. It emphasizes the potential benefits of a native macOS authenticator while acknowledging the importance of robust security considerations, thoughtful design, and ongoing maintenance.
In-Depth Analysis¶
Mactokio represents a design philosophy that prioritizes reducing friction in security-critical tasks. By moving TOTP generation from a separate mobile device to the desktop, the project aims to deliver a more efficient login experience without compromising on security fundamentals. For many users, minutes saved per login accumulate into a noticeably smoother daily workflow, especially for those who frequently access services protected by 2FA.
Key aspects likely addressed by Mactokio include:
Verification Code Generation: TOTPs are generated locally on the Mac, synchronized with a shared secret and time-based algorithms. The user’s experience is simplified because codes appear within the macOS environment, avoiding context switches between devices.
Open-Source Ethos: As an open-source project, Mactokio invites community scrutiny, collaboration, and transparency. This approach helps build trust among users who rely on verifiable security mechanisms rather than proprietary implementations.
Platform Integration: A native macOS app has the potential to leverage system features, such as secure storage, background updates, and smooth integration with macOS security controls, while maintaining a familiar look and feel for Mac users.
Security Considerations: Any desktop authenticator must address how secrets are stored, protected, and backed up. The model for enrollment, backup recovery, and potential recovery from device loss becomes a central design consideration.
User Experience: The emphasis on eliminating the “phone detour” highlights a broader focus on usability without sacrificing security. A well-designed desktop authenticator should minimize friction while preserving robust protection against impersonation and phishing attempts.
Attack Surface and Threat Model: Moving 2FA code generation to the desktop shifts the risk landscape. It requires careful attention to device security, phishing resilience, and trust in the environment where codes are displayed and used.
Recovery and Synchronization: For users who replace devices or reinstall software, mechanisms for transferring authenticator credentials are essential. This includes secure backup options, migration paths, and recovery workflows that protect against accidental disclosures.
Dependency on Local Hardware: By removing the reliance on a phone, the solution emphasizes the security and resilience of the user’s computer. However, it also concentrates risk on a single device, underscoring the need for strong password protection, biometric safeguards, disk encryption, and regular software updates.
Community and Adoption: The success of an open-source solution like Mactokio often hinges on community adoption, ongoing maintenance, and compatibility with a broad range of services that rely on TOTPs.
Comparisons with Existing Solutions: Other authentication flows may rely on hardware keys (such as FIDO2 U2F devices) or push-based verification. A desktop authenticator sits within a spectrum of options, offering a different balance between convenience and hardware requirements.
Impact on Security Practices
Convenience vs. Security: The core trade-off is the balance between user convenience and preserving strong authentication. Reducing the steps to obtain a code can improve compliance with 2FA, provided the desktop environment remains secure.
Data Protection: Securing secrets used for TOTP generation is critical. This may involve secure enclaves, protected keychains, or other hardware-assisted protections that reduce risk if the system is compromised.
Device Compromise: If an attacker gains control of the Mac, they could potentially access TOTPs. Consequently, device hardening, user vigilance, and timely patching become even more critical when relying on a desktop authenticator.
Backup and Recovery: Users must be able to recover their credentials if their Mac is lost or damaged. A robust recovery strategy must be in place to prevent loss of access to important services, especially those that enforce strict 2FA requirements.
Phishing Resistance: TOTPs are inherently vulnerable to phishing if an attacker can prompt the user to reveal a code. A desktop authenticator must consider user education, anti-phishing safeguards, and potential integration with phishing-resistant methods like push-based approvals or hardware keys.
*圖片來源:Unsplash*
User Experience and Accessibility
Streamlined Workflows: By eliminating the need to switch devices, users can complete the authentication step more rapidly, reducing login latency and improving productivity.
Visual Clarity: A well-designed macOS app can present codes clearly, with legible typography and accessible color contrast, mitigating the squinting problem described in the original experience.
On-Device Security: Local storage of secrets should be protected with macOS security features, including strong sandboxing, keychain integration, and encrypted storage.
Cross-Device Considerations: For households or teams that rely on shared accounts, synchronization and policy management become important. A desktop authenticator should support scenarios where multiple devices are involved in organizational security.
Future Implications
Shifting Security Paradigms: The rise of native desktop authenticators could influence how services implement 2FA. If desktop-native solutions gain traction, service providers may rely more on secure device ecosystems rather than external apps on mobile devices.
Ecosystem Compatibility: Widespread adoption depends on compatibility with services that generate or accept TOTPs. Interoperability standards and security practices will shape how easy it is to migrate between devices or platforms.
Innovation in 2FA: The desktop approach might pave the way for more integrated, user-friendly security tools, including advanced recovery options, richer UX, and deeper integration with platform security features.
Community-Driven Security: Open-source projects benefit from community contributions, audits, and transparency. This can lead to faster vulnerability discovery and more rapid patching, increasing overall trust in the solution.
Potential Risks and Critiques
Single-Device Dependency: Relying on a Mac for 2FA can be problematic if the device is unavailable or compromised. Contingency plans, like hardware keys or backup methods, are essential to maintain access to critical accounts.
Secrets Management: The security of TOTPs hinges on how secrets are stored and accessed. If secrets are inadequately protected, the entire authentication process could be at risk.
Platform Lock-In: A macOS-focused solution may alienate users on other platforms or those who need cross-platform consistency for organizational policies.
Adoption Barriers: Some users may prefer established mobile-based or hardware-based 2FA methods due to familiarity, perceived security, or existing infrastructure.
Key Takeaways
Main Points:
– A native macOS authenticator can reduce login friction by eliminating phone-based 2FA steps.
– Open-source design encourages transparency, collaboration, and continuous improvement.
– Security considerations, including secret management, recovery, and phishing resilience, are central to the solution.
Areas of Concern:
– Ensuring robust backup and recovery while protecting sensitive data.
– Addressing the risk of device compromise and single-device dependence.
– Maintaining cross-service compatibility and avoiding vendor lock-in.
Summary and Recommendations
The concept behind Mactokio reflects a broader trend toward integrating security tools directly into the devices people use daily. By delivering a native macOS authenticator, the project targets a smoother user experience without sacrificing core security properties. The open-source nature of the project adds a valuable layer of transparency and community involvement, which can lead to more rigorous security practices and faster adaptation to evolving threats.
For individuals considering adopting a native macOS authenticator, several recommendations emerge:
– Evaluate your threat model: If you prioritize convenience and have strong device security, a desktop authenticator can be a compelling option. If you rely on multiple devices or operate in high-risk environments, you may want to complement it with additional factors or hardware keys.
– Ensure robust device security: Enable full-disk encryption, use strong passwords, and consider biometric protections and up-to-date software to reduce the risk of credential access.
– Plan for backup and recovery: Implement a secure backup strategy for your authenticators, and understand the recovery processes provided by the solution and the services you use.
– Stay vigilant against phishing: Recognize that TOTPs can be susceptible to phishing. Consider combining desktop authenticators with phishing-resistant methods where feasible.
In the end, Mactokio represents an intriguing attempt to streamline secure access by bringing 2FA code generation closer to the user. Its success will depend on careful attention to security architecture, thoughtful UX design, and sustained maintenance in a landscape that increasingly values both security and convenience.
References
– Original: https://dev.to/dalirnet/i-built-a-native-macos-authenticator-app-because-i-was-tired-of-reaching-for-my-phone-5899
– Additional references:
– NIST Digital Identity Guidelines (section on 2FA and TOTPs)
– FIDO Alliance resources on phishing-resistant authentication
– Mac security best practices and keychain storage guidance
*圖片來源:Unsplash*