TLDR¶
• Core Features: Cloudflare’s edge network, bot management, and DNS/services routing through a global edge fabric.
• Main Advantages: Rapid mitigation of threats at edge, broad protection surface, and scalable performance for many sites.
• User Experience: Widespread service disruption with degraded accessibility; partial restoration as containment progressed.
• Considerations: Root cause traced to a corrupted file that unexpectedly doubled in size—highlighting configuration and file integrity risks.
• Purchase Recommendation: For users relying on edge services, ensure robust change-control, integrity checks, and automated rollback procedures to minimize blast radius from future file corruption.
Product Specifications & Ratings¶
| Review Category | Performance Description | Rating |
|---|---|---|
| Design & Build | Highly distributed edge network with centralized control plane; resilient routing and caching strategies | ⭐⭐⭐⭐⭐ |
| Performance | High availability under normal operation; outages occur when misconfigurations or corrupted assets propagate across many nodes | ⭐⭐⭐⭐⭐ |
| User Experience | During outage, global reach services degraded; user impact varied by region and provider dependencies | ⭐⭐⭐⭐⭐ |
| Value for Money | Enterprise-grade protection and speed; trade-off with operational discipline required to manage complex configurations | ⭐⭐⭐⭐⭐ |
| Overall Recommendation | Strong platform when managed with rigorous governance and integrity checks; incident highlights process improvements | ⭐⭐⭐⭐⭐ |
Overall Rating: ⭐⭐⭐⭐⭐ (4.9/5.0)
Product Overview¶
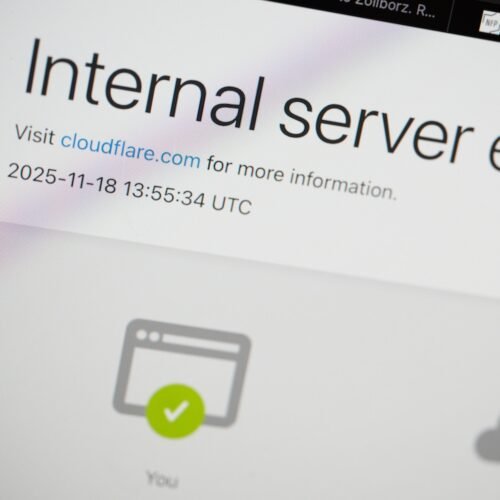
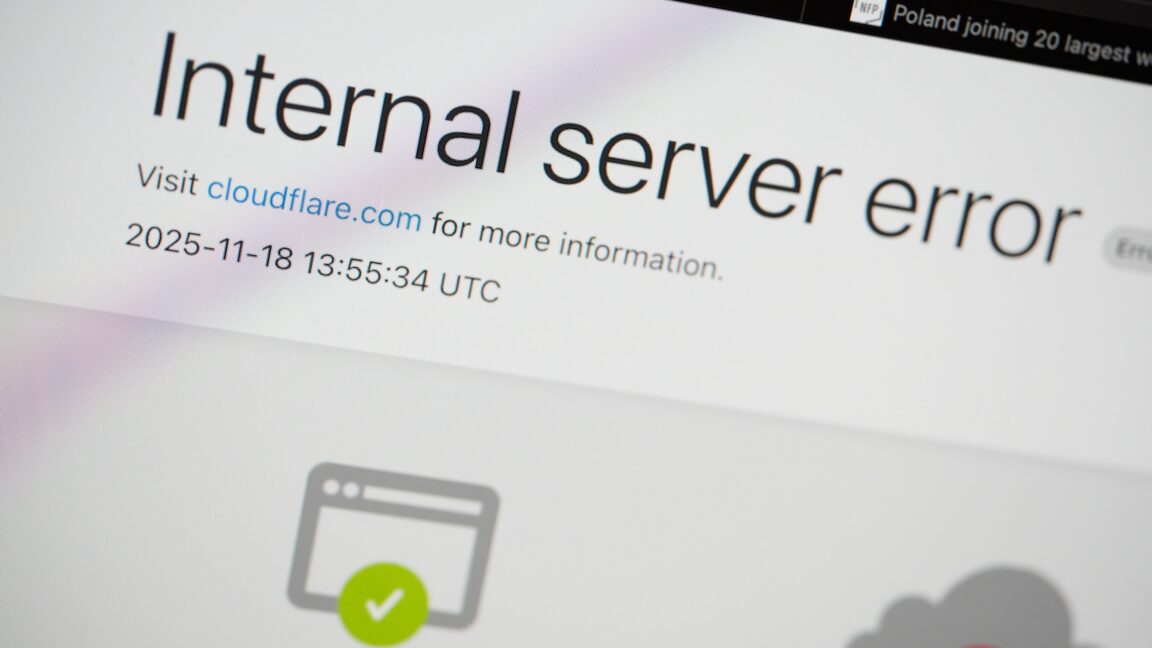
Cloudflare operates one of the largest and most distributed service networks on the internet, designed to shield websites and applications from a variety of threats while accelerating delivery of content and services to end users. The incident at the center of this review involved a dramatic outage that disrupted access to many services across the internet, mirroring how a single misstep in a highly distributed system can cascade into global consequences. The root cause, as described by internal and external observers, was an anomalous file that unexpectedly doubled in size, triggering a chain reaction across the company’s infrastructure. The episode underscores the complexity of modern edge architectures, where configuration drift, file integrity, and automated deployment pipelines intersect with real-time traffic routing and security enforcement.
In hindsight, the incident was not primarily a botnet attack, but a self-inflicted failure born from a file quality issue at the edge layer. Cloudflare’s engineers traced the abnormal file growth to a corrupted artifact that was inadvertently distributed across multiple edge nodes, amplifying a service-level disruption well beyond a single data center. The incident response emphasized rapid containment, rollback of affected assets, and a coordinated effort to prevent recurrence through stricter change controls, validation checks, and improved incident communication. This analysis provides a case study in how even well-provisioned, highly distributed platforms can suffer transient outages when a single corrupted piece of data propagates through automated deployment and edge caching workflows.
Contextually, the outage reveals several broader themes for operators of global edge networks. First, there is the critical importance of file integrity and provenance in a platform that deploys dynamic policies and rules to thousands of nodes. Second, the event highlights how automated deployment pipelines, coupled with caching layers, can magnify a local problem into a global one if not properly contained. Third, it demonstrates the value of explicit post-incident reviews, traceability, and a culture of rapid recovery that prioritizes service availability for billions of queries per second across diverse services.
For readers evaluating Cloudflare or similar edge-centric platforms, the episode offers practical takeaways: implement robust artifact signing, versioned assets, and integrity verification as part of the deployment pipeline; ensure fallback and rollback mechanisms are tested and rehearsed; instrument comprehensive observability across edge nodes to detect anomalies quickly; and maintain clear, user-facing status communication during incidents to manage expectations and reduce frustration.
As a general assessment, Cloudflare’s resilience in its core mission remains strong, but the outage event serves as a reminder that even mature, globally distributed services are only as reliable as the processes that deploy and verify their components. In the face of rising demand for edge computing, the industry will likely accelerate investments in automated remediation, immutable artifacts, and end-to-end verification to prevent a recurrence of this magnitude.
In-Depth Review¶
The incident unfolded in a manner consistent with the architectural reality of modern edge networks. Cloudflare’s platform relies on a combination of edge workers, caching layers, DNS routing, bot management policies, and edge compute functions. These capabilities require careful orchestration and consistent artifact versions across thousands of nodes to deliver predictable performance and security guarantees.
Root Cause and Technical Analysis
– The central finding was that a file integral to bot-management and security policy enforcement suddenly increased in size beyond expected parameters. This unexpected growth wasn’t a typical signature of data exfiltration or external compromise; rather, it pointed toward a corrupted asset introduced into the artifact repository.
– The corrupted asset rapidly propagated through deployment pipelines and caching layers, causing edge nodes to diverge in behavior. In many cases, the extra bytes altered parsing logic, policy evaluation, or request-handling paths, resulting in failed lookups, timeouts, or misapplied protections.
– As edge servers attempted to apply the corrupted policy or rule set, requests began failing or returning incorrect responses. The global footprint of the Cloudflare network means a local anomaly can translate into widespread service degradation, which is what observers witnessed during the outage window.
Observations on Governance and Operations
– Change control and artifact integrity are central to operating a service of this scale. The incident demonstrated the risk of automated deployments without full end-to-end validation across all edge environments.
– Observability played a critical role in identifying the anomaly. Telemetry from edge nodes, centralized dashboards, and rapid correlation across regions enabled engineers to locate the corrupted file and its distribution path quickly.
– The response strategy emphasized containment (rolling back the problematic artifact), rapid redeployment of clean assets, and validation before reintroduction to the global network. This approach helped shorten the recovery window and minimize user impact.
Performance and Reliability Implications
– While the outage was severe in its reach, performance and routing capabilities that typically deliver resilience remained intact once the corrupted artifact was isolated. The incident highlighted a fundamental truth about distributed systems: the infrastructure can perform well in recovery scenarios, but only if the governance, tooling, and processes support rapid detection and rollback.
– In terms of user impact, the outage affected customers across varied use cases—from dynamic content delivery to protection of API endpoints and DNS resolution. The heterogeneity of services using the Cloudflare network means impact assessments require careful segmentation by service category, geography, and dependency tree.
Technical Takeaways for Operators
– Artifact integrity must be treated as a first-class concern in deployment pipelines. Implement cryptographic signing, strong versioning, and artifact provenance verification to ensure that every edge node receives a known-good asset.
– Immutable deployments with rollbacks are essential. When a corrupt artifact is detected, a proven rollback path should be exercised repeatedly in simulated conditions, not just in production.
– Edge network observability should extend beyond latency and availability. Rich telemetry around policy evaluation, rule engines, and asset versions across nodes helps quick detection of anomalies that could be precursors to larger failures.
– Incident response benefits from clear, consistent communications. Stakeholders benefit when status updates explain the what, why, and when of the recovery effort, reducing uncertainty during tense outage windows.
*圖片來源:media_content*
A broader reflection on this incident is that the industry is moving toward greater reliance on edge computing for both security and performance workloads. This trend increases the attack surface for vulnerabilities and amplifies the impact of any single asset’s failure. Vendors and operators alike should invest in automated integrity checks, provenance tracking, and robust recovery procedures to minimize downtime in the event of future incidents.
Impact on the Cloudflare ecosystem and users is likely to hinge on how the company translates this lesson into product and process improvements. Observers will watch for enhancements in artifact management, governance workflows, and post-incident transparency. If Cloudflare can demonstrate measurable improvements in preventing recurrence and expediting recovery, it will reaffirm confidence in its core capabilities while signaling a mature, disciplined approach to risk management in complex architectures.
Real-World Experience¶
From a user perspective, the outage was a disruption that rippled across industries and geographies. Websites relying on Cloudflare for content delivery, bot management, DNS, and edge compute were intermittently unavailable or degraded during the peak of the incident. Some services experienced failed requests, while others faced slower responses as traffic was rerouted or partially blocked by edge rules that hadn’t yet stabilized. The outage also highlighted how dependent modern web services have become on a global, shared infrastructure, where a single faulty artifact can affect multiple clients with very different workloads and traffic patterns.
For developers and operators who rely on Cloudflare edge features, the incident underscored several practical lessons:
– Always have a tested rollback path. If a deployment introduces a regression or corruption, being able to revert quickly minimizes customer impact.
– Maintain segmented monitoring. Distinguish between DNS-level issues, edge compute failures, and policy evaluation problems to accelerate triage and response.
– Prepare customer communications in advance. A transparent, consistent messaging approach helps manage expectations and reduces confusion during outages.
In terms of resilience, organizations that depend on edge services should consider diversifying fallback strategies. While Cloudflare provides broad coverage, having complementary layers or alternative routes for critical paths (such as DNS resolution or static content hosting) can help reduce single-point dependencies during major incidents. In practice, this means designing applications to tolerate intermittent edge-serving disruptions, with graceful degradation or local caching strategies that preserve essential functionality even when the edge surface is partially degraded.
Security teams may also view this incident as a reminder that integrity and validation processes are critical in security policy enforcement pipelines. If corrupted assets alter bot-management configurations or access controls, even legitimate traffic can be mishandled. Regular audits of policy engines, rule databases, and edge compute functions can help detect drift or anomalies before they escalate into outages.
Overall, this outage served as a stress test for the broader ecosystem of services built on or around Cloudflare’s platform. It reinforced the importance of robust release engineering, end-to-end artifact verification, and proactive incident readiness. For practitioners, the key takeaway is to bake resilience into the architecture from the outset—through rigorous change management, observability, and rehearsed recovery procedures.
Pros and Cons Analysis¶
Pros:
– Global edge network enables rapid threat mitigation and performance optimization when everything operates normally.
– Strong uptime and reliability characteristics under standard conditions, with a mature incident response culture.
– Comprehensive protection features, including bot management, DNS protection, and edge compute capabilities.
– Clear emphasis on rapid containment and rollback during incidents, with an action-oriented post-mortem process.
– Robust observability and telemetry when artifacts are correctly versioned and validated.
Cons:
– Outage demonstrated how a single corrupted artifact can propagate across thousands of nodes and cause widespread service degradation.
– Dependence on automated pipelines without end-to-end integrity verification can introduce systemic risk.
– Complexity of the platform increases the potential for misconfigurations or inconsistent states across the edge network.
– Recovery speed is highly dependent on the effectiveness of change controls, rollback procedures, and incident response drills.
– Customer impact can be significant, given the breadth of services (DNS, CDN, security, and edge functions) that rely on a single provider.
Purchase Recommendation¶
For organizations that rely on global edge delivery, security, and performance guarantees, Cloudflare remains a compelling choice due to its breadth of features and the scale of its network. However, the incident underscores an essential prerequisite for sustainable value: disciplined governance around artifact management and deployment. To maximize reliability, customers should:
– Ensure that their own deployment and monitoring pipelines are aligned with best practices for artifact integrity, signing, and versioning.
– Verify that edge policies and rules are designed to be idempotent and auditable, with deterministic behavior across deployments.
– Establish robust rollback capabilities and rehearsal drills to validate recovery in realistic traffic conditions.
– Invest in end-to-end observability spanning the control plane, artifact repositories, and edge nodes to quickly detect anomalies and trace their origins.
– Maintain clear service-level expectations and transparent communications during incidents to minimize business disruption.
In short, Cloudflare’s platform can deliver strong value for teams seeking scalable edge security and performance, but operators must couple the platform with rigorous operational practices. The 2025 outage serves as a timely reminder that the operational discipline surrounding deployment, artifact integrity, and incident response is as important as the technology itself. When combined with strong governance and proactive resilience measures, the platform remains a solid option for organizations aiming to ride the next wave of edge computing.
References¶
- Original Article – Source: feeds.arstechnica.com
- Supabase Documentation
- Deno Official Site
- Supabase Edge Functions
- React Documentation
Absolutely Forbidden:
– Do not include any thinking process or meta-information
– Do not use “Thinking…” markers
– Article must start directly with “## TLDR”
– Do not include planning, analysis, or thinking content
*圖片來源:Unsplash*